FIREWALL CM Presentation
-
Upload
chandan-dutta -
Category
Documents
-
view
236 -
download
0
Transcript of FIREWALL CM Presentation
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 1/17
FIREWALL
PRESENTED BY
AJEET KERKETTA(183)CHANDAN DUTTA(190)
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 2/17
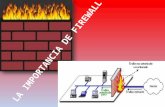
What is a Firewall?
A firewall is hardware, software, or a combination
of both that is used to prevent unauthorizedprograms or Internet users from accessing a
private network and/or a single computer
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 3/17
Hardware vs. Software Firewalls
Hardware Firewalls
± Protect an entire network
±
Implemented on the router level ± Usually more expensive, harder to configure
Software Firewalls
± Protect a single computer
± Usually less expensive, easier to configure
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 4/17
How does a firewall work ?
Inspects each individual packet of data as it
arrives at either side of the firewall
Inbound to or outbound from your computer Determines whether it should be allowed to
pass through or if it should be blocked
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 5/17
Firewall Rules
Allow traffic that flows automatically
because it has been deemed as safe (Ex.
Meeting Maker, Eudora, etc.)
Block traffic that is blocked because it has
been deemed dangerous to your computer
Ask asks the user whether or not the traffic
is allowed to pass through
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 6/17
Firewall approach
it provides numerousadvantages to sites byhelping to increase overallhost security
1. Protection from VulnerableServices
2. Controlled Access to SiteSystems
3. Concentrated Security4. Enhanced Privacy
5. Logging and Statistics onNetwork Use, Misuse
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 7/17
Protection from Vulnerable Services
improve network securityand reduce risks to hosts onthe subnet
prohibit certain vulnerable
services such as NFS fromentering or leaving aprotected subnet
permits the use of theseservices with greatly
reduced risk to exploitation protection from routing-
based attacks
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 8/17
Controlled Access to Site Systems
Ability to control accessto site systems.
Do not provide access to
hosts or services that donot require access
A user requires little orno network access to
desktop workstation,then a firewall canenforce this policy
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 9/17
Concentrated Security
most modified additionalsecurity software couldbe located on the firewallsystems as opposed to
being distributed onmany hosts.
opposed to each systemthat needed to beaccessed from the
Internet. simpler to implement to
run specialized software.
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 10/17
Enhanced Privacy
Normally be consideredinnocuous information thatwould be useful to anattacker.
Some sites wish to blockservices such as finger andDomain Name Service.
Firewall used to block DNSinformation about site
systems. The names and IP addresses
systems would not beavailable to Internet hosts.
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 11/17
Logging and Statistics on Network Use,
Misuse
firewall can logaccesses and providevaluable statistics
about network usage with appropriate
alarms that soundwhen firewall andnetwork are beingprobed or attacked
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 12/17
Types of firewalls
1.packet filtering
firewalls
2.circuitlevel gateways3.application gateways
4.stateful multilayer
inspection firewall
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 13/17
Advantages of firewall Concentration of security
Protocol filtering
Information hiding
Application gateways ,
Extended logging
Centralized and simplifiednetwork services management
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 14/17
Disadvantages of firewall
Certain types of networkaccess may be hampered forsome hosts, telnet, ftp, XWindows, NFS, NIS, etc
A firewall system is that itconcentrates security in onespot as opposed to distributingit among system.
A firewall cant protect against
attacks that dont go throughthe firewall.
Firewalls can't protect wellagainst things like viruses.
8/3/2019 FIREWALL CM Presentation
http://slidepdf.com/reader/full/firewall-cm-presentation 15/17
Conclusion
In conclusion inter net isthe dangerous place..
Without firewall not
connected to inter net. Fire wall protect private
file from outsiders.
Firewall providenecessary security forsuch type of illegalaccess.
































![Presentation-Understand Solar [CM-203]](https://static.fdocuments.ec/doc/165x107/58ee2d871a28ab58598b46c9/presentation-understand-solar-cm-203.jpg)

